iCSS hosts the 24th International Conference on Information and Communications Security (ICICS 2022)
16 November 2022

This year, iCSS hosted the 24th International Conference on Information and Communications Security (ICICS 2022) at the main campus of the University of Kent, in Canterbury, Kent, UK. The conference took place over four days, from 5 to 8 September, and hosted a number of presentations and demonstrations, both in-person and online.
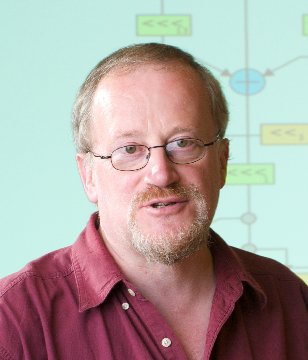 The first keynote of the conference, 'Future Challenges in Security Engineering', was presented by ProfessorRoss Anderson, Professor of Security Engineering at University of Cambridge and University of Edinburgh, UK. In this talk, Professor Anderson discussed how the right to software updates for goods with digital elements will affect durable safety-critical goods with software and network connections, like cars and medical devices. If a customer expects software updates for a reasonable time period after purchase, how will teams support security patches and safety for 10+ years, for example? This challenge becomes more complex when taking into account machine learning components, as well as associated costs and practical design limits.
The first keynote of the conference, 'Future Challenges in Security Engineering', was presented by ProfessorRoss Anderson, Professor of Security Engineering at University of Cambridge and University of Edinburgh, UK. In this talk, Professor Anderson discussed how the right to software updates for goods with digital elements will affect durable safety-critical goods with software and network connections, like cars and medical devices. If a customer expects software updates for a reasonable time period after purchase, how will teams support security patches and safety for 10+ years, for example? This challenge becomes more complex when taking into account machine learning components, as well as associated costs and practical design limits. The third keynote, 'Toward Practical Privacy Protections for Blockchain Networks', was presented by Dr Guang Gong, a professor in the Department of Electrical and Computer Engineering at University of Waterloo, Canada. In this talk, Dr Gong examined the current research in permissionless and permissioned blockchain systems and their potential for applications where value or data is transferred, stored and processed. Dr Gong also provided an example of Zero-Knowledge Succinct Non-Interactive Argument of Knowledge (zk–SNARK) schemes.
The third keynote, 'Toward Practical Privacy Protections for Blockchain Networks', was presented by Dr Guang Gong, a professor in the Department of Electrical and Computer Engineering at University of Waterloo, Canada. In this talk, Dr Gong examined the current research in permissionless and permissioned blockchain systems and their potential for applications where value or data is transferred, stored and processed. Dr Gong also provided an example of Zero-Knowledge Succinct Non-Interactive Argument of Knowledge (zk–SNARK) schemes.In addition to the three keynotes, at the Conference there were a total of 11 technical sessions, each of which included 3-4 papers. Visit our website for more information on the programme, or watch the recorded presentations on YouTube.
This year's event also saw winners of six awards:
Congratulations to all of the award winners!
iCSS were delighted to welcome so many visitors to Kent and thank the authors, the presenters and everyone who helped to organise and run the day.

